FINCII2024 CYBER DRILL OSINT MALVERTISING
Walkthrough
Question 1: File Hash: 96f8bda7e072baf4a55e1c3557f6d79d30a7eb5432294019536e28cfa07cce82. Find the associate file name with extension.
It was an easy one. Just searching the file hash on Google brings up several links related to the file hash.
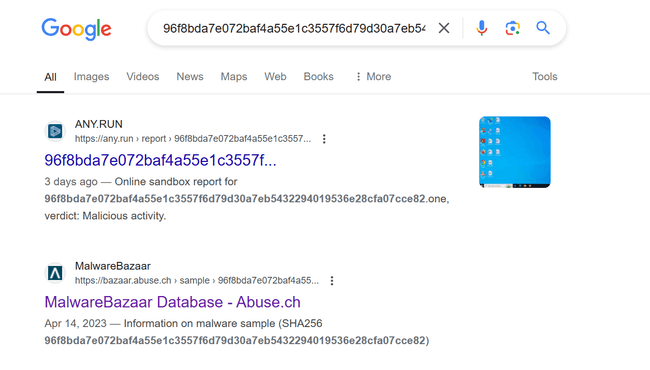
By visiting any of these sites, you should get the filename with extension. But an even easier way is searching on Virustotal. I searched in VirusTotal and found the filename was review.one.
Question 2: An embeded executable found in the downloaded file. Find the SHA-256 hash value of the executable.
Under the "Relations" tab, in the "Bundled Files" section, there is a windows installer named install.msi. Clicking on the installer reveals the hash. By googling and researching a little bit we can confirm the exact hash.
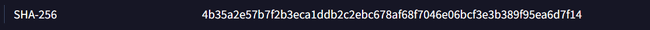
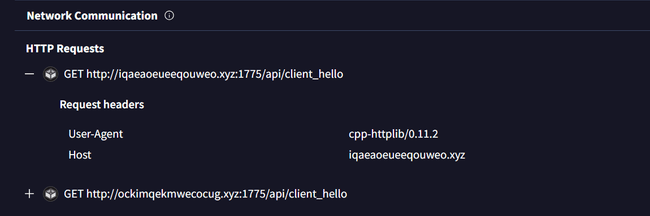
Question 3: Find the user-agent that the above executable used for network communication.
After searching the hash on VirusTotal, go to the "Behavior" tab, and within that, open the "Network Communication" section. In this section, under "HTTP Requests," you’ll find the user-agent used by the executable.
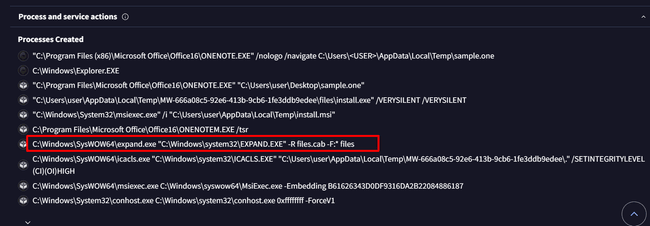
Question 4: The malware executed a shell command to extract inflated MetaStealer EXE from a file. What was the command?
In the "Behavior" tab, under "Process and service actions" in the "Processes created" section, I found the command used. Since the question is related to extracting a file, the command should also be related to file extraction. The command C:\Windows\SysWOW64\expand.exe "C:\Windows\system32\EXPAND.EXE" -R files.cab -F:* files matches this.
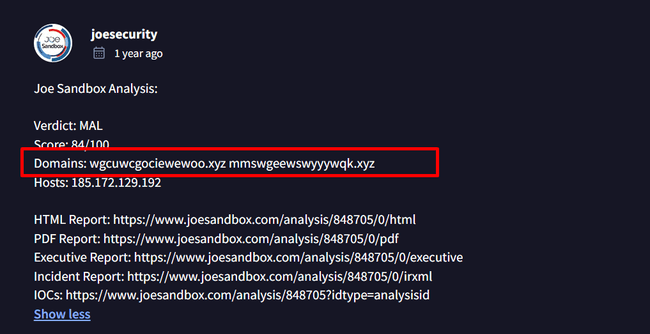
Question 5: Find the associate domains for IP 185.172.129.192 which belongs to MetaStealer.
In the "Community" tab, I reviewed comments and found a note from joesecurity that listed the domains associated with the IP.
Please pardon any mistakes. Have question? Connect with me on LinkedIn